Sitting listening to one of the speakers whilst attending the ‘M2M: Beyond Connectivity’ seminar hosted by European Communications this week, for a moment I was reminded of the classic football chant – “Who ate all the pies?” The general consensus is that the chant was originated by Sheffield United supporters at the end of the 19th century and aimed at their 140kg goalkeeper. Not sure he would be playing in the top flight nowadays!!
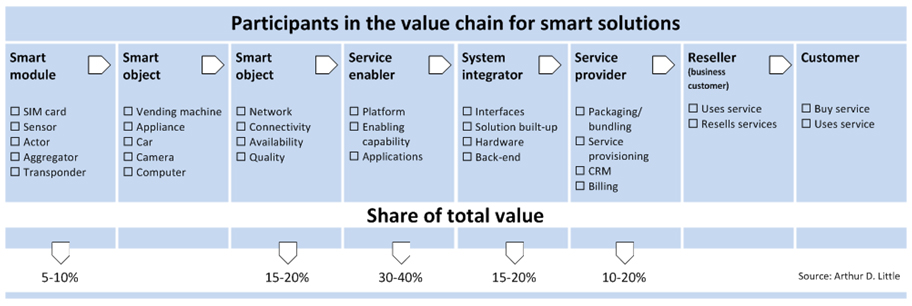
So what was it that led me to draw a parallel between an overweight football player and M2M? In the presentation by Ansgar Schlautmann from Arthur D. Little, an interesting and revealing view of the holistic value chain for smart solutions was given.
The individual players in the spread of total revenues need not however be concerned by the splits shown; even in fact for the CSPs who see their connectivity portion with a distribution of somewhere between 15-20%. With the anticipated value of the M2M market projected to reach approximately $86 billion[i] by 2017, even this slice of the pie should be enough to get their teeth into.
The analogies associated with balanced nutrition and how the industry will ensure that each participant will get its own healthy share can be drawn in a number of ways, so let’s consider them.
Use by
If we have to be honest, it’s a good thing that the M2M industry has come to us with a long shelf life. It’s been a number of years to even get us to this point where we see on the horizon a potential explosion of new product/service offerings being crafted for the market.
There will always be those people who want to be early adopters and will derive the niche, well crafted packaged service for their market, but surely one of the keys here is to just start thinking M2M in all areas of our lives, we need to start using it, to start realising the potential it can bring to daily routine where in a sense – decisions are made for us. This isn’t to a Skynet level, albeit the goal there was for speed and efficiency and to reduce human error – even though M2M can bring us that. To reap the benefits of M2M, we need to build it, we need to use it, when by? The sooner the better.
Best before
Even though we can get excited by cars that will arrange their own services; highway maintenance being done based upon vehicular data relating to potholes; smart cities that will see routine maintenance programmes scrapped for self servicing provisioning and so on – the reality is we are a little way from reaching this best before point. Now I say best before not in the context of a product/service will expire in it’s usefulness at some point in the future. I mean with regards to when we will see offerings come to us as consumers that will encapsulate all of the richness that M2M could potentially bring to us. It is getting closer, advancements are being made in all sectors of the industry, but to reach a best before point – I don’t see that happening until we see wholehearted adoption within the verticals themselves.
Ingredients
Having the right ingredients, i.e. providing energy, protein, carbohydrates etc. in the right quantity, quality and packaging in many cases are a key factor when we hit the supermarket or the online grocery sites. As consumers in this M2M arena, will we be so different? We want well packaged, well balanced, quality products and services. As participants in this M2M value chain, the balance will come from the blend of services that can be offered; the partnerships that are built; being able to craft simple, yet wholesome solutions to the consumer flavour of the day.