Regulators train their sights on SIM Swap. What should telcos do?
In April 2018, Gregg Bennett, an entrepreneur in Bellevue, Washington, noticed something odd happening across his email account, after which his phone connectivity immediately zeroed out. Fearing a hacking attempt, Bennett, unfortunately, could do little as the fraudsters took control of his phone number via his SIM, therein gaining access to Bennett’s Amazon, Evernote, Starbucks, and even his Bitcoin account, whereby he lost 100 Bitcoin.
Greg Bennett was a victim of SIM swapping.
SIM swapping is a form of digital identity theft that banks on ‘social engineering.’ Often recognized as the second phase of a fraud attack, SIM swapping happens when fraudsters take control of a victim’s mobile number and from there obtain verification codes like OTPs and URNs that give them unfettered access to protected accounts.
The trick: How does SIM Swapping work?
I’ve often likened the finesse of SIM swapping to the sleight of a hand seen at a magic show. One moment the magician directs your attention to the object, perhaps a bird cast in flight. The next second, it vanishes, and as your eyes remain distracted trying to fathom the disappearing act, the real magic trick unfolds in the shadows: The bird pops up into existence somewhere unexpected – a pleasant surprise, a round of applause, a delighted audience.
But unlike the joy audiences feel at seeing the friendly flutter of feathers again, the ripple effect of SIM swapping is unpleasant and notably sinister.
Scammers take control of a replacement SIM that is replaced through spurious methods such as reporting a handset lost or stolen, placing requests for SIM replacement, or producing fake documents to get a duplicate SIM. Today, mobile phones are the nerve center of authentication for myriad transactions. So, it doesn’t take more than a few steps thereafter to grant hackers access to personal accounts.
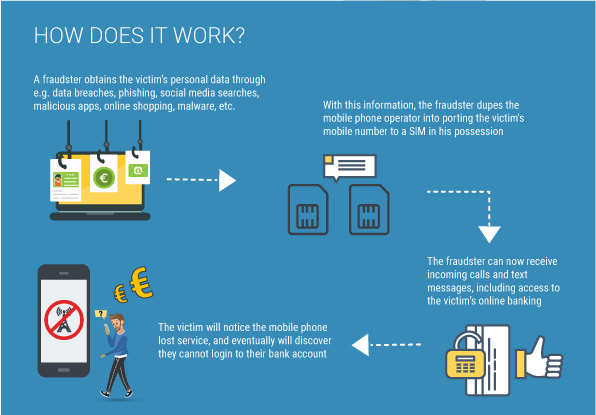
Fun, Funds, and Fame – Motives of SIM Swap Crime
Money, certainly, is a driving factor. In the UK alone, SIM swapping cost telecom operators £2.9 million, with over 3,000 cases registered in 2018. In their 2019 IC3 Report, the FBI notes how arresting a leader of a SIM swapping group leader led to the seizure of over US $18 million, five vehicles, a US $900,000 home, and hundreds of thousands of dollars in jewellery. Which.co.uk reported a story about Garth Pollard, a victim of a SIM swapping attack where the attacker spent £13,000 over 48 hours.
But some hackers engage in SIM swaps simply for the fun of it.
Take the case of Ruby, whose Instagram handle @ruby was much desired by some of the platform’s users. When Ruby turned out many requests to sell her handle, one hacker decided to scam it off her using a SIM swap. Her provider, AT&T, took note of her complaint and restored her phone number, but it took Ruby much longer to regain her beloved Insta-handle.
No matter the motive behind the fraud, SIM-jacking is a menace for customers. It also exposes telecom providers to a series of negative effects through lawsuits arising from non-compliance and inadequate consumer protection.
Seamlessness versus Security – The Telco Dilemma
It almost makes you wonder why telecoms aren’t doing more to stop this fraud. A chief research officer and expert in the field holds the view that higher security barriers for SIM registrations detract from the ‘seamless experience’ telcos wish to provide their customers. In an effort to make customer acquisition easier, telecoms just might be leaving a window open for SIM swappers to manipulate the system and create trouble for existing customers.
There is light at the end of the tunnel! Just like how a magician’s repetitive tricks force us to bypass the legerdemain, regulators are now training their sights on SIM swappers.
The loophole lies in mobile number portability vulnerabilities, which is what the US Federal Communications Commission (FCC) hopes to fix with its new slew of rules. Some of these include introducing a ‘port freeze’ whereby customers can opt to disable SIM duplication requests to avert ‘port out fraud.’ As stated in its recent press release, the FCC proposes that phone carriers be required to securely “authenticate a customer before transferring a phone number to a new device or carrier.”
African telcos are adopting countermeasures, too. Safaricom, the Kenyan telecom provider, has created an API that alerts banks when a customer’s SIM has been swapped, allowing the bank to decisively protect the customer’s commercial accounts from fraud attacks. African telecoms have also attempted to tighten SIM registration processes in the hope of dissuading scammers. But in emerging markets where standardized national identities are owned by far fewer citizens than there are mobile users, enforcing such dictates (and the efficacy of it) is yet to be known.
So, how do you begin to protect yourself?
Creating awareness, protecting privacy, and fostering healthy scepticism among end-users in the online world is a good place to start.
What does this look like? Think about being cautious when installing apps from non-trusted sources. Refrain from clicking on non-verified links, check before downloading files from unknown senders, and use protocols to keep data private. These are actionable guidelines and advice everyone can follow by default.
As end-users, here are some tips from Europol (in the infographic) that we can use to minimize the risk of becoming a victim of SIM swaps:

For telecom organizations, a robust defense strategy with multi-layered defense mechanisms, as listed below, can help stay ahead of SIM swap:
- Features such as link analysis in fraud management systems can analyze, in a visual manner, the different events that are under investigation. This helps anti-fraud analysts understand data patterns from the records and take faster action against fraudsters.
- AI/ML capabilities support understanding subtle differences in user behavior, thus averting instances of SIM swap fraud before they escalate.
- Implementing strong process controls such as:
Subex Fraud Management has built-in capabilities that handle different types of fraud, including SIM Swap, per regional compliance norms.
Discover more about how Subex Fraud Management helps you sidestep SIM swapping


