Mobile Money is Rewriting the Fraud Landscape in Africa
Users across the globe are rapidly adopting digital wallets to shop, transact, and pay for utilities using mobile money. Easy, convenient, and real-time, these services are proliferating, particularly in markets where banking access is limited. Take Africa, for example, in just a few years, it has raced ahead as the global leader in the mobile payments landscape, with nearly 161 million active accounts and more than 495 billion dollars in transactions.
In 2020, this mushrooming industry got new impetus.
Crippled by COVID-19 in what GSMA calls the ‘Great Lockdown of 2020’ in its recent report State of the Industry on Mobile Money 2021, the world was pushed into a recession, limiting the movement of goods and exchange of cash. But in this crisis, mobile money providers seized their inherent advantages to empower economies by providing financial assistance. Here too, Africa leads the way. The GSMA report states that “In 2020, Sub-Saharan Africa continued to account for the majority of growth with 43% of all new accounts.”
When we think of mobile money in Africa, M-PESA may be the first name that pops to mind – and rightly so. They were the first player to roll out mobile wallets that doubled up as pseudo-bank accounts. Prolific smartphone access has amplified this trend, extending mobile money beyond banking to something people can use for nearly every service, including booking flights, buying insurance, shopping, foreign remittances, and more. A 2020 report titled Mobile Money and Organized Crime in Africa states that “In September 2019, there were 153 active mobile money operators operating in 45 African countries.” Clearly, this market shows no signs of slowing down.
Origin of risk
Every new technology comes with a certain risk, and mobile money is no exception. Running these services means establishing multiple and complex back-end integrations with different players, each of which adds to the risk surface. It has drawn the attention of hackers/fraudsters worldwide as they turn their efforts to exploiting pressure points in the mobile money ecosystem.
What is worrying is that these loopholes aren’t hard to find.
Weak ID verification systems, poor customer awareness, insufficient security resources, inadequate training, and limited access to best-in-class fraud detection tools are all challenges that make breaches and financial theft possible.
Regulations are another challenge. Most regulators are struggling to keep pace with how fast the technology is advancing. Striking a balance between user experience and data safety is a constant wrestle. Moreover, as laws take time to catch up, the criminal justice system lags at apprehending offenders. The African Mobile Money report captures this succinctly, stating, “The lack of resources and training of law enforcement concerning the collection and use of technical evidence in the criminal justice system has resulted in difficulties in prosecuting offenders and tackling established organized crime groups.” Further, the low onboarding barriers for mobile money make it a lucrative channel for terrorist financing and money laundering via cross-border payments and international remittances. Without the right checks and balances and cross-country governing rules, mobile money regulatory frameworks tend to be weak, leading to cracks in implementation, particularly pan-country, making it harder to monitor money laundering activities.
So, what does mobile money fraud look like?
Briefly, these include:
- Customer Acquisition Frauds – Abuse of identity documents to create fake accounts on the platform.
- Identity Theft – This involves SIM swaps where fake ID proof is used to procure duplicate SIM cards for online transactions, leading to account takeovers.
- Transaction Frauds: The mobile money account holder can perform an increasing number of transactions. The number and variety of operations have grown immensely in the recent past. Some of the types of transactions are as follows:
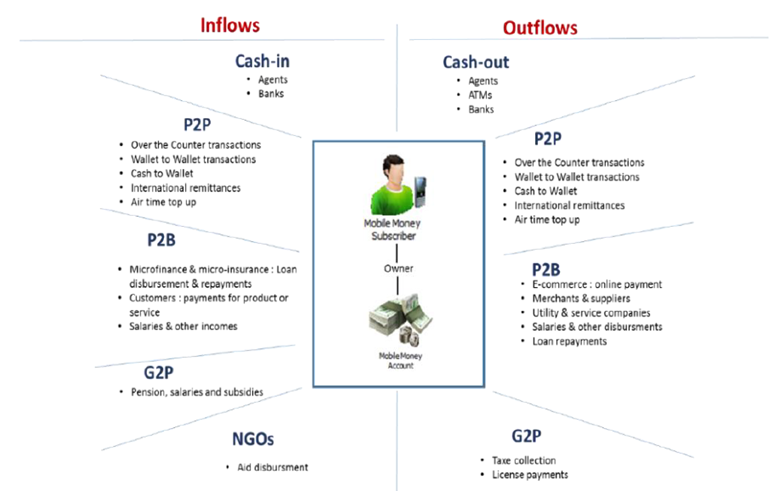
Source:https://enactafrica.org/research/interpol-reports/mobile-money-and-organised-crime-in-africa
However, fraudsters can exploit various loopholes in these processes to commit fraud. In transaction frauds, stolen cards, data, or accounts are used to perform unauthorized transactions like income tax refunds, fake social media accounts, phishing, etc.
- Money Laundering –Money laundering is the illegal process of making large amounts of money generated by criminal activity, such as drug trafficking or terrorist funding, appear to have come from a legitimate source. Money launderers can exploit mobile money services to transfer the proceeds of crime to co-conspirators located in other countries, or supporters of terrorist organizations can exploit.
- Internal Frauds – Frauds conducted internally by merchants or employees with access to customer information.
Uganda’s mobile money network took a significant hit on October 3, 2020, when one of the companies providing services to telecom companies was exploited by fraudsters, leading to 3.2 million stolen dollars. The theft was executed through unsuspecting telecom companies, and money was exchanged through mobile money payment systems using 2000 SIM cards. Many reasons are implicated in the execution of this fraud, including malicious telecom agents, fake KYC, and spurious campaigns.
Clearly, the challenges of verification and identification are the weakest links. Without being able to clarify whether transactions are authentic, issues like money laundering for terrorist financing emerge. As stated in the Mobile Money and Organized Crime in Africa report, the sheer diversity of national ID documents as well as low national ID coverage in Africa further compound this challenge.
Need for a Multi-Pronged Strategy
With mobile money adoption rates increasing in Africa bearing the promise of even more growth, mobile operators and digital wallet companies need a proactive mindset to stay ahead of fraud. Well-defined training programs, for instance, can educate customers and internal teams on the different types of fraud risk and vectors. Implementing the right fraud management tool, which has the capability to monitor suspicious activity related to internal employees, partners, agents, sanctioned lists, etc., and outfitted with robust AI/ML capabilities that track millions of daily transactions and detect abnormal behavior is extremely important. Further, when coupled with Anti-Money Laundering (AML) capabilities like risk categorization, suspicious activity monitoring, and AML watchlists, such solutions provide a robust defense, helping operators ensure themselves from the evils of mobile money fraud.
Subex enabled a Tier-1 African Operator to uncover Mobile Money Fraud and help them save USD 3 million




