The Re-Emergence of Convergence
Operators and global industry forums continue to wrestle with the question of whether or not to merge their fraud and security teams/work-groups to cope better with criminals who are breaking in through IP-based networks in order to derive profit for themselves (or their causes), or just to wreak havoc and disruption on their “enemies”. Fraudsters are not just partaking in the traditional crimes of bypass fraud, roaming, Dial Through, AIT/PRS, Call Selling fraud etc., but also the exciting new stuff…. Phishing, malware, spoofing, DDoS, Trojans etc.
One can be forgiven for thinking that fostering closer links between fraud and security domains is breaking new ground in terms of responding to the threats posed by 4G/LTE, NextGen, the continued growth of e/m-commerce and the proliferation of data passing over networks. I guess it is a sign of my advancing years that I can’t help feeling that we have been here before…
15 years ago, when I was prepping for an interview for my first job in the fraud management arena, I was listening open-mouthed as a fraud expert was explaining to me the finer points of PBX Hacking. Thinking back, two things were very clear:-
- The Operator in the UK already had a merged fraud and security group (which they later separated out, then subsequently re-merged again, by the way).
- The main advice to combat PBX Hacking was prevention, not detection… and that meant security prevention. The operator was keen to tell its business customers that they needed to physically lock away their PBX equipment, protect their passwords, switch off unnecessary/vulnerable services such as DISA/Voicemail, carry out security awareness training for switchboard operators, support staff, suppliers, use barring at switch or extension level, keep PBX call logging records to see hacking attempts before they succeed, shred old copies of internal directories, vet their security/cleaning staff, etc. etc. The FMS only stepped in when all the prevention activities failed and the PBX was breached. By the time that happened, operators were already losing money directly, if they were responsible for the switch, or indirectly if their customers were liable. Customers may have been unwittingly facilitating the fraud by their lack of security awareness etc. but even so, if a small business – used to paying perhaps $1000 a month for calls, suddenly gets a bill for $20000, they are going to fight it, refuse to pay it or be unable to pay it. The indirect cost to the operator of customer complaints, disputes, potential court cases, damage to the brand, bad publicity, negotiated settlements, debt write-off and churn etc. can cost far more than the original bill. It was a lose/lose situation… unless you were the fraudster.
These days, with the emergence of 4G/LTE, IP-based Networks, perpetrators are still committing the same underlying crime for the same motives as before, but now they are breaking in through a host of different entry points, wearing better disguises, carrying bigger SWAG bags and using faster getaway vehicles. In truth, many operators are struggling to keep up with the high number and seemingly unpredictable nature of these attacks.
Security teams are traditionally very good at preventing access to networks, but they are not perfect. The pace at which network elements, components, interfaces and transactions are increasing is making it impossible for all the preventative measures to be in-situ from day one. Not to mention the surfeit of off-the shelf tools that fraudsters can use to break in to more and more lucrative areas of daily commerce.
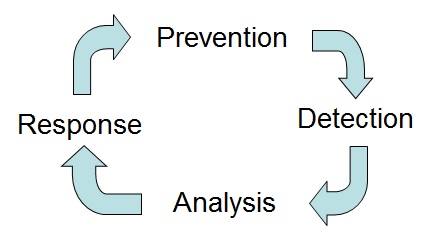
In practice, Prevention alone cannot succeed. Detection, Analysis and Response are also essential elements of the fraud management cycle.
So, my point is this…. security and fraud teams cannot operate in silos. Security teams must continue to try and prevent malicious intrusion as much as possible. That requires taking in a lot of real-time data from the access points, identifying the nature of the content and the data patterns and quickly blocking anything that looks dubious. But when the intruder gets in (and they do in their numbers), that is when the fraud team can also play their part.
Whilst the security team controls corporate IT networks, how well can they police the mobile workers and the homeworkers, the tablet users, the App Store/Android Users etc.? And if you think that profiling subscribers was difficult historically, how much harder is it when you can’t even define what a subscriber is, let alone track their behaviour. In the new world, the relationship between account holder, subscriber and product/service is not always obvious. Also, the billing relationships for transactions can be mind-boggling. Couple this with the speed at which these transactions are taking place and the value of services and content being passed across a proliferation of bearers, and you have a minefield to negotiate.
This is where a good Fraud Management System can supplement an operator’s security tools. An FMS must now be equipped to take in much larger volumes of data than before, in many different forms and process it much quicker. Any reputable FMS vendor will now be offering solutions with large scale, flexible data handling tools (including probe / deep packet inspection events), internal/sales partner audit logs/feeds, inline service/transaction monitoring, exhaustive rules engines (real-time, in-line and statistical), subscriber grouping & profiling features, reference data including Hotlists/Blacklists, fraud and device “fingerprinting” capabilities, ID verification, alarm prioritisation and established, flexible workflows, with a range of analytics tools and visualisation features. All these components – in the hands of an experienced and well-managed fraud operations outfit – will help to choke fraudsters and drive them out to look for easier targets.
So, in summary, don’t let the security guys take all the strain at the prevention stage. Share the data, share the knowledge and spread the load to the fraud team for a more comprehensive response.
To get more information about Subex Fraud products please click here.
Product Manager for Fraud & Credit Risk Products in Subex. – John has more than 35 years’ experience in the telecoms industry working in a variety of different roles and activities from engineering to Product Management via Project Management, Marketing, Programme Management, Presales and more….
He is a well-respected Subject Matter Expert in the area of fraud management and operations with a wealth of experience to draw on.
John is also a qualified Project Manager with accreditation from International Project Management Association (IPMA) and is an active participant in the Telecommunications UK Fraud Forum (www.tuff.co.uk) – having been accredited by TUFF with Distinction as a Telecommunications Fraud Professional.
Request a demo