- SOLUTIONS
- SERVICES
- ABOUT US
- RESOURCES
- CONTACT
SIMBox Fraud: Challenges and AI-Powered Solutions for Telecom Operators
As global communication expands, so does the sophistication of fraud schemes targeting telecom operators. Among these, SIMbox fraud has emerged as one of the most severe challenges facing the industry. This type of fraud costs telecom companies billions of dollars annually, affecting service quality, compromising security, and threatening business growth. With increasing cross-border communication, SIMbox fraud has grown into a global problem that affects both emerging and developed markets.
In this blog, we will explore how SIMbox fraud operates, its impact on the telecom industry, and the AI-powered solutions that telecom operators can adopt to detect and combat this growing menace. Additionally, we’ll analyze global trends in SIMbox fraud, examine case studies, and explore AI/ML methodologies for fraud detection, with an eye on future trends in combating this evolving threat.
What is SIMBox Fraud?
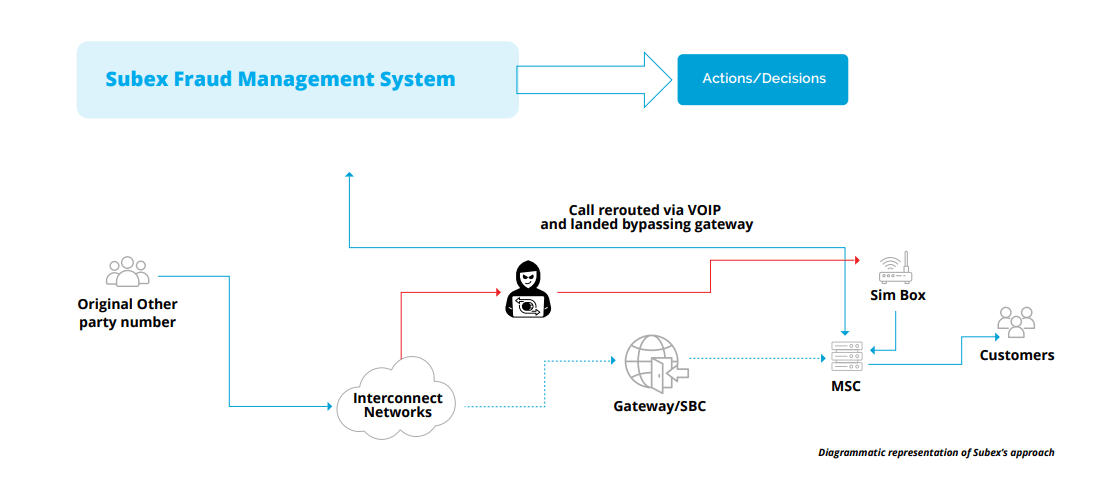
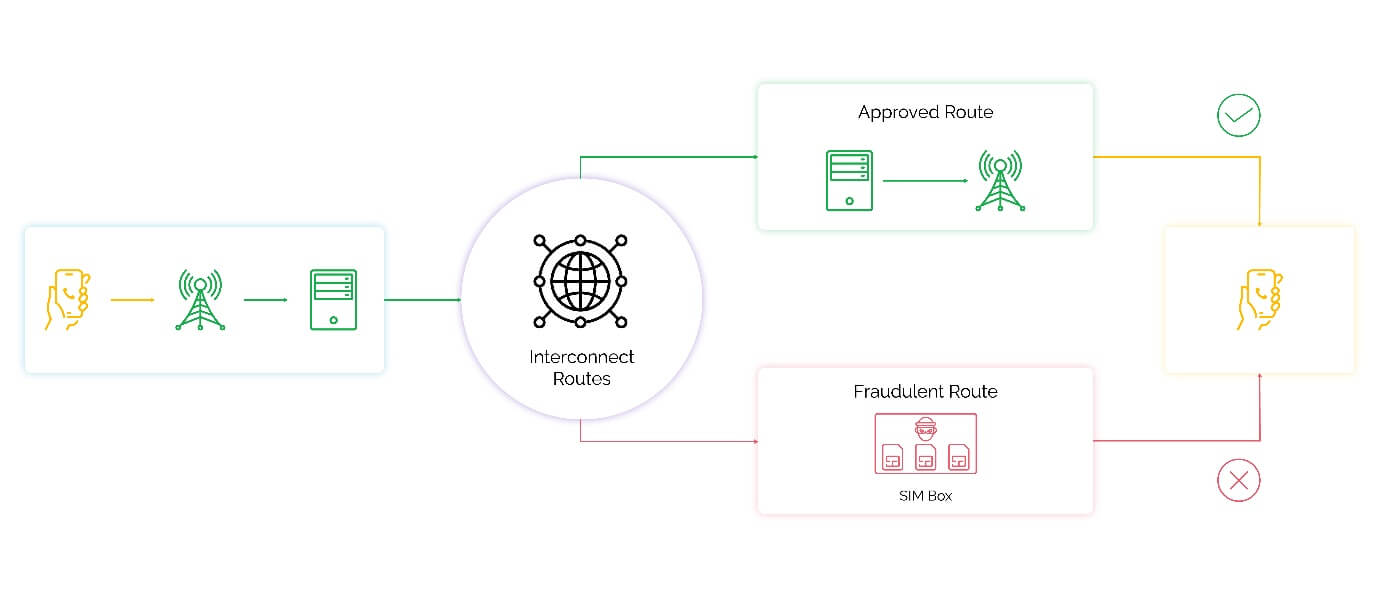
At its core, SIMbox fraud (also known as interconnect bypass fraud) exploits the price disparity between local and international call rates. Fraudsters use a device called a SIMbox, which contains multiple SIM cards purchased from various mobile network operators (MNOs). These SIM cards are used to bypass official international gateways, routing international calls as local ones via Voice over Internet Protocol (VoIP) systems.
The process involves rerouting international calls through internet gateways and local SIM cards, masking the international origin of the call. The SIMbox operators profit by avoiding the high international tariffs, while the telecom companies suffer from revenue loss. SIMbox fraudsters also exploit weak regulatory frameworks in some regions, using SIM cards obtained via fraudulent means, including stolen or fake identities.
SIMBox fraud is one of the top telecom frauds in terms of the revenue loss to telcos. CFCA, in its Global Fraud Loss Survey in 2023, estimated that Voice Interconnect Bypass fraud alone costs around $5.06 billion globally, making it one of the top 5 fraud types.
How SIMBox Fraud Works
- Multiple SIM Cards: Fraudsters insert numerous SIM cards into the SIMbox, each connected to a local network. These SIMs act as the gatekeeper for international calls. Typically, fraudsters purchase prepaid SIM cards in bulk or exploit promotions offering cheaper local rates. To avoid detection, they rotate SIM cards frequently, ensuring none stay active long enough to raise suspicion. Additionally, sophisticated SIM boxes can manage hundreds of SIM cards, automatically swapping them in and out to prevent rapid deactivation by telecom operators. This mass deployment of SIM cards allows the fraudster to bypass traditional international calling fees while remaining under the radar of anti-fraud systems.
- VoIP Routing and Optimization: Calls are routed through a broadband connection using VoIP (Voice over Internet Protocol) technology, avoiding international tariffs. Fraudsters often use multiple VoIP providers to avoid detection and ensure uninterrupted service. They sometimes optimize the call routing by selecting paths that offer the lowest latency and cost, further reducing their operational expenses. Advanced fraudsters may also implement automatic call distributors (ACDs) to manage call flow, minimizing call drops and maximizing the efficiency of their illicit operations. Additionally, some SIMbox operators may use encrypted VoIP channels to make detection even harder for telecom operators.
- Local Number Spoofing: The SIMbox manipulates the caller ID to show a local number associated with one of the SIM cards, hiding the true international origin of the call. This method of caller ID spoofing makes it look as though the call is originating from within the local country, fooling both users and telecom systems. Fraudsters often use dynamically generated numbers, which may correspond to genuine users, further complicating detection efforts. This technique helps to bypass anti-fraud filters that would flag international calls being terminated as local. Some advanced SIMboxes also change the caller ID in real-time, based on the destination of the call, to avoid repeated detection.
- Call Termination: By bypassing official gateways, the call is transmitted via a local network, leading to significant revenue loss for the telecom provider. The call termination process exploits local termination rates, significantly undercutting the legitimate revenue stream of telecom operators. Since the calls never pass through official international routes, the operator cannot charge standard international rates. Furthermore, this rerouting can cause call quality issues for end-users, including poor audio quality, call drops, and delays. Over time, excessive fraud through SIM boxes can deteriorate the overall service experience for genuine users and erode customer trust in the network. This form of termination fraud also negatively impacts telecom operators’ reputation, as they face growing operational costs from implementing countermeasures and regulatory fines.
Why SIMBox Fraud Is a Growing Threat
The proliferation of SIMbox fraud is not accidental; it is driven by several factors:
- Global Communications Boom: In recent years, especially during and after the pandemic, there has been a massive increase in global communication. Remote work, online conferencing, and international calls have become the norm. This surge in communication has created new opportunities for fraudsters to exploit the price differentials between local and international call rates. SIM boxes allow fraudsters to bypass legitimate network infrastructure, rerouting international calls through local numbers, and thus avoiding the higher costs associated with cross-border calls. This exploitation of arbitrage opportunities in telecom tariffs has only grown more lucrative as international communications have expanded.
- High Call Termination Costs: Countries with particularly high call termination fees, such as Cuba, Seychelles, and Algeria, are attractive targets for SIMbox fraud. Fraudsters leverage these high costs to maximize their profits by routing international calls through local networks at significantly reduced rates. For telecom operators in these countries, the loss of revenue due to SIMbox fraud is especially damaging, as it undercuts their ability to fairly charge for the infrastructure and service they provide. Furthermore, the illegal rerouting of traffic results in poor service quality for end-users, increasing complaints and damaging the operators’ reputations.
- Weak SIM Card Regulations: Many emerging markets have lax regulations around the sale and use of SIM cards. Fraudsters exploit this by purchasing large quantities of SIM cards using fake identities or by taking advantage of countries where SIM card registration is not strictly enforced. The lack of robust Know Your Customer (KYC) requirements means that fraudsters can operate SIM boxes with little fear of being tracked or held accountable. In countries where SIM cards can be purchased anonymously or with minimal documentation, SIMbox fraud continues to thrive, allowing criminals to set up and operate fraud schemes with relative ease.
- Technological Advances in Fraudulent Practices: As telecom operators have improved their ability to detect and prevent SIMbox fraud, fraudsters have adapted their methods. The use of automated and sophisticated systems allows fraudsters to scale their operations, often controlling hundreds or even thousands of SIM cards remotely. Additionally, advanced techniques like IMEI spoofing, IP anonymization, and the use of virtual SIM cards make it more difficult for operators to pinpoint the exact location or identity of the fraudsters.
A particularly concerning evolution is Human Behavior Simulation (HBS), where fraudsters program SIM boxes to mimic normal user behavior—making short-duration calls, sending SMS, changing cell locations, and even using mobile data. This deceptive mimicry allows fraudulent SIMs to blend in with genuine users, making detection even harder for systems relying on static thresholds or conventional analytics. - Lower Cost of Entry: The equipment needed to set up a SIMbox operation has become cheaper and more accessible. Fraudsters can now acquire the necessary hardware and software at a relatively low cost, making it easier for small-scale operators to enter the space and contribute to the growing threat. This low barrier to entry has resulted in a proliferation of SIMbox fraud networks across various geographies, further complicating the efforts of regulators and operators to contain the problem.
- Impact on Network Performance and Security: SIMbox fraud not only causes significant revenue losses but also degrades the quality of service for legitimate customers. The rerouting of traffic through SIM boxes often leads to network congestion, dropped calls, and poor voice quality. Additionally, it poses security risks, as these illicit setups can be used to mask more nefarious activities such as smuggling of calls for illegal purposes, making it harder for law enforcement to track communication activities.
The Challenges of Traditional SIMBox Fraud Management
Current SIMbox fraud detection techniques are not adequate as they don’t promise a foolproof approach to detect this fraud in near real-time. For example, Call Data Record (CDR) analysis, while delivering comprehensive coverage, falls short in addressing the issue of earlier detection and high false positives associated with such methods.
A standard CDR analysis can identify abnormal rises in call volume from a single number and provide metrics like the ratio between incoming and outgoing calls, and local vs. international calls. However, these figures may not always give accurate results because bypass fraud patterns differ across countries, operators, and networks. Fraudsters often stay below detection thresholds or simulate human-like behavior to evade detection.
Test Call Generator (TCG) analysis performs better in terms of accuracy for threat detection, but it struggles with coverage and predictability. Fraudsters can even simulate genuine network behavior to compromise the system and generate manipulated events.
Additionally, SIMbox perpetrators have become smarter, using methods to avoid detection, such as:
- Use of Anti-Fraud Detection Methods: Techniques like sending SMSs, simulating data sessions, receiving calls, HBS, changing cell sites, etc., are used to make fraudulent activity appear legitimate.
- Automated Software: Fraudsters reprogram Equipment IDs to bypass detection systems.
- Deceptive Detection: Fraudsters allocate pools of SIM cards to be purposely detected or captured, creating positives.
Rule-based systems have long struggled with balancing detection sensitivity, set thresholds too low, and fraud slips through undetected; set them too high, and false positives overwhelm analysts. These limitations can be effectively addressed with advanced technologies like Artificial Intelligence (AI), Machine Learning (ML), and Generative AI (GenAI)-powered agents. AI/ML models not only learn to distinguish between genuine and fraudulent behavior with higher precision but also adapt to evolving fraud patterns. GenAI-powered agents further augment this by autonomously investigating anomalies, correlating multi-source data, and guiding analysts with actionable insights. This shift from static rules to intelligent systems enables telcos to detect SIMbox fraud in real time while minimizing both detection gaps and operational noise.
The Impact of SIMBox Fraud on Telecom Operators
The implications of SIMbox fraud are far-reaching and detrimental to telecom operators. Let’s explore some of the key challenges:
- Revenue Loss: The most direct impact of SIMbox fraud is the revenue loss it causes. Telecom companies lose billions annually due to the rerouting of international calls, undermining their profitability.
- Service Quality Degradation: SIM boxes often use cheap, substandard setups that lead to poor call quality, dropped calls, and connection delays.
- Compromised Security: SIMbox fraud bypasses encryption and security protocols, allowing unauthorized interception of sensitive communications.
- Infrastructure Strain: The large volume of rerouted calls can overload local networks, causing congestion and damage to telecom infrastructure.
- National Security Threat: SIMbox fraud evades legal monitoring systems, allowing it to be used for criminal activities like terrorism and smuggling.
How AI/ML Helps Combat SIMBox Fraud
As SIMbox fraud becomes more complex, traditional detection methods such as CDR and TCG analysis are no longer sufficient. AI/ML provides a more sophisticated approach to fraud detection, offering enhanced coverage and predictive capabilities.
1. Anomaly Detection
AI/ML systems can analyze vast amounts of Call Detail Records (CDRs) and detect unusual patterns of behavior indicative of SIMbox fraud. These systems use algorithms to differentiate between normal and suspicious call behavior, providing real-time alerts to operators.
2. Predictive Analysis
Machine learning models can predict future fraudulent activities by recognizing trends in past fraud incidents. This predictive capability helps operators proactively block fraud before it occurs.
3. Real-Time Detection
AI-powered systems can monitor network traffic in real-time, detecting fraudulent activities as they happen. This ensures that operators can prevent financial losses by blocking fraudulent calls immediately.
4. Geographic Anomaly Detection
Fraudsters often exploit geographic anomalies by routing international calls through local SIM cards. AI-based geographic filtering can track and block calls with unusual geographic origins, adding an additional layer of defense.
5. Investigation Analysis by AI Agents
AI Agents assist fraud analysts by autonomously investigating suspicious call patterns, correlating data from multiple sources, and generating actionable insights. These agents can automate time-consuming analysis, suggest next-best actions, and even simulate fraud scenarios to help teams understand and respond to threats faster and more effectively.
6. Self-Learning Algorithms
Machine learning algorithms are capable of self-learning from new fraud patterns, allowing them to adapt and evolve as fraudsters develop new techniques. This ability to continuously improve detection accuracy is a key advantage of AI/ML-based solutions.
AI/ML and GenAI – The New Mantra for Telcos
Enterprises seeking to acquire next-generation capabilities are increasingly turning to AI, ML, and now GenAI to drive innovation, boost agility, and unlock new value from existing business models. For telcos, who sit on a goldmine of user and network data, these technologies open the door to transformative possibilities—from minimizing customer churn to enhancing network performance in real time.
Extending these capabilities to fraud detection empowers telcos to effectively counter sophisticated threats like SIMbox fraud. While traditional methods such as CDR/TCG analysis remain valuable, integrating them with AI/ML provides enriched seed data and enables more adaptive, intelligent fraud detection systems.
By combining historical call analysis with real-time AI/ML insights and GenAI-powered investigative support, telcos can adopt a truly holistic approach. This fusion offers the best of both worlds: precise detection, broader threat coverage, and the agility to respond to evolving fraud patterns faster than ever before.
Case Study: The Role of AI in Combating SIMBox Fraud
A Tier-1 telecom operator in the Asia Pacific region faced significant challenges with SIMbox fraud, a growing threat that impacted both revenue and customer experience. To address this issue, the operator partnered with Subex to deploy an AI-driven fraud detection system. Over a 12-month period, the AI solution analyzed a vast dataset of Call Detail Records (CDRs), identifying irregular patterns and detecting fraud in near real-time. The implementation resulted in the following key outcomes:
- Achieved a 98% fraud detection hit rate, vastly improving fraud detection compared to the legacy system.
- Improved fraud detection by 175% compared to the operator’s previous fraud management system.
- Reduced the mean time to detect fraud to just 8 minutes, allowing for quicker response and resolution.
- Prevented additional losses by 60%, significantly safeguarding revenue.
- Reduced customer complaints by 31%, enhancing the overall customer experience by minimizing fraud-induced disruptions.
This case study demonstrates how AI-driven solutions not only mitigate fraud but also drive operational efficiency, improve customer satisfaction, and protect revenue for telecom operators.
Preventing SIMBox Fraud: Best Practices for Telecom Operators
SIMbox fraud is a dynamic and complex issue, but telecom operators can implement several key strategies to mitigate its impact. Here are some best practices:
- Secure SIM Card Management: One of the fundamental steps to prevent SIMbox fraud is to ensure robust SIM card lifecycle management. Telecom operators should secure the distribution, storage, and activation of SIM cards to limit fraudulent actors’ access. Implementing stringent KYC (Know Your Customer) processes and real-time monitoring of SIM card usage can reduce the likelihood of exploitation.
- AI/ML and GenAI for Fraud Detection and Investigation
Implementing a robust AI and machine learning-based solution is essential in detecting SIMbox fraud in real-time. AI models can continuously analyze call detail records (CDRs) and other metadata to identify suspicious patterns indicative of fraud. With machine learning algorithms capable of adapting to new fraud techniques, operators can stay ahead of evolving threats.Adding to this, GenAI-powered agents can significantly enhance fraud investigation workflows. These intelligent agents can assist fraud analysts by automating data correlation, generating insights from large volumes of structured and unstructured data, and recommending the next-best actions. This not only reduces the burden on human teams but also accelerates time-to-detection and response. - International Collaboration: Working closely with global carriers, regulatory bodies, and law enforcement agencies is vital in the fight against SIMbox fraud. Sharing intelligence on emerging fraud tactics, traffic patterns, and suspicious activities allows operators to combat cross-border fraud more effectively. Fraudsters often operate in multiple countries, making collaboration essential in shutting down their networks.
- Geographic Filtering and Anomaly Detection: Analyzing call metadata and filtering out geographic anomalies can significantly reduce fraudulent activity. This can be done by detecting unusual patterns in call origination and termination points that are indicative of SIMbox activity. By utilizing AI-powered analytics, operators can stay ahead of these patterns and flag irregularities that may suggest fraud.
- Randomized Testing: Performing randomized tests to various call destinations can reveal unusual routing paths and highlight potential SIMbox fraud. Testing both local and international calls ensures that operators can identify when calls are being rerouted illegally and take action to mitigate these activities.
- Legal and Contractual Safeguards: Operators should not rely solely on technical fixes. Strengthening legal frameworks is another essential layer of protection. Collaborating with legal teams to update contracts and include fair usage policies can prevent abuse by unscrupulous partners. Ensuring that contracts limit bulk SMS usage or define stricter controls for traffic allowances will deter fraudsters from exploiting weaknesses in commercial agreements.
- Product and Pricing Adjustments: Telecom operators should regularly evaluate their product offerings and pricing models from the perspective of fraudsters. Operators should work with their commercial teams to fine-tune product offerings to be more fraud-resistant and reduce the financial incentives for SIMbox fraud.
Conclusion: Subex’s AI-Powered SIMBox Fraud Solutions
SIMbox fraud continues to evolve in complexity and scale, posing a persistent threat to telecom operators globally. Traditional detection methods, while still useful for foundational coverage, are no longer sufficient to combat the increasingly sophisticated tactics used by fraudsters, including the use of automated SIM management, caller ID spoofing, and Human Behavior Simulation (HBS). These evolving methods demand more intelligent, adaptable, and real-time defenses.
Subex’s AI-powered approach provides a robust response to this challenge. By combining Machine Learning, Artificial Intelligence, and GenAI-powered agents, with traditional analytics, Subex enables telecom operators to detect fraud faster, more accurately, and with minimal false positives. These systems go beyond static thresholds, continuously learning from new fraud patterns and generating real-time insights to empower fraud analysts with the right actions at the right time.
As fraudsters continue to innovate, telcos must do the same—adopting AI-first strategies that not only detect but also prevent SIMbox fraud proactively. With the right technology stack, international collaboration, and fraud intelligence, operators can safeguard their revenues, protect their networks, and deliver a secure, high-quality experience to their customers.
Q1. What is a SIMbox?
A SIMbox is a device used to route international calls through a VoIP system, bypassing official gateways and masking the call as a local one to avoid international tariffs.
Q2. What is SIMbox fraud?
SIMbox fraud is a type of telecom fraud where fraudsters use SIM boxes to reroute international calls as local ones, allowing them to profit from the price difference between local and international call rates.
Q3. What is VoIP?
VoIP (Voice over Internet Protocol) is a technology that enables voice calls to be transmitted over the internet instead of traditional telephone lines. In the context of SIMBox fraud, VoIP is exploited by fraudsters to reroute international calls through internet gateways, disguising them as local calls to avoid international tariffs.
How it works:
VoIP converts voice signals into digital data, which is then sent over broadband networks. Fraudsters use this capability to bridge international calls into local networks using SIM cards, bypassing legitimate international gateways.
Relevance to SIMBox Fraud:
- Cost Avoidance: By leveraging VoIP, fraudsters drastically reduce call costs.
- Caller ID Spoofing: VoIP makes it easy to manipulate caller information.
- Scalability: It allows mass call rerouting with minimal infrastructure costs.
- Detection Difficulty: VoIP routes are often encrypted or anonymized, making detection harder for telcos.
Q4. How does SIMbox fraud affect telecom operators?
SIMbox fraud causes revenue loss, damages service quality, compromises security, and can strain telecom infrastructure, ultimately affecting customer trust and business growth.
Q5. How can AI help detect SIMbox fraud?
AI-powered solutions can analyze call patterns, monitor voice quality, track geographic anomalies, and manage SIM cards in real-time, enabling operators to detect and mitigate SIMbox fraud efficiently.
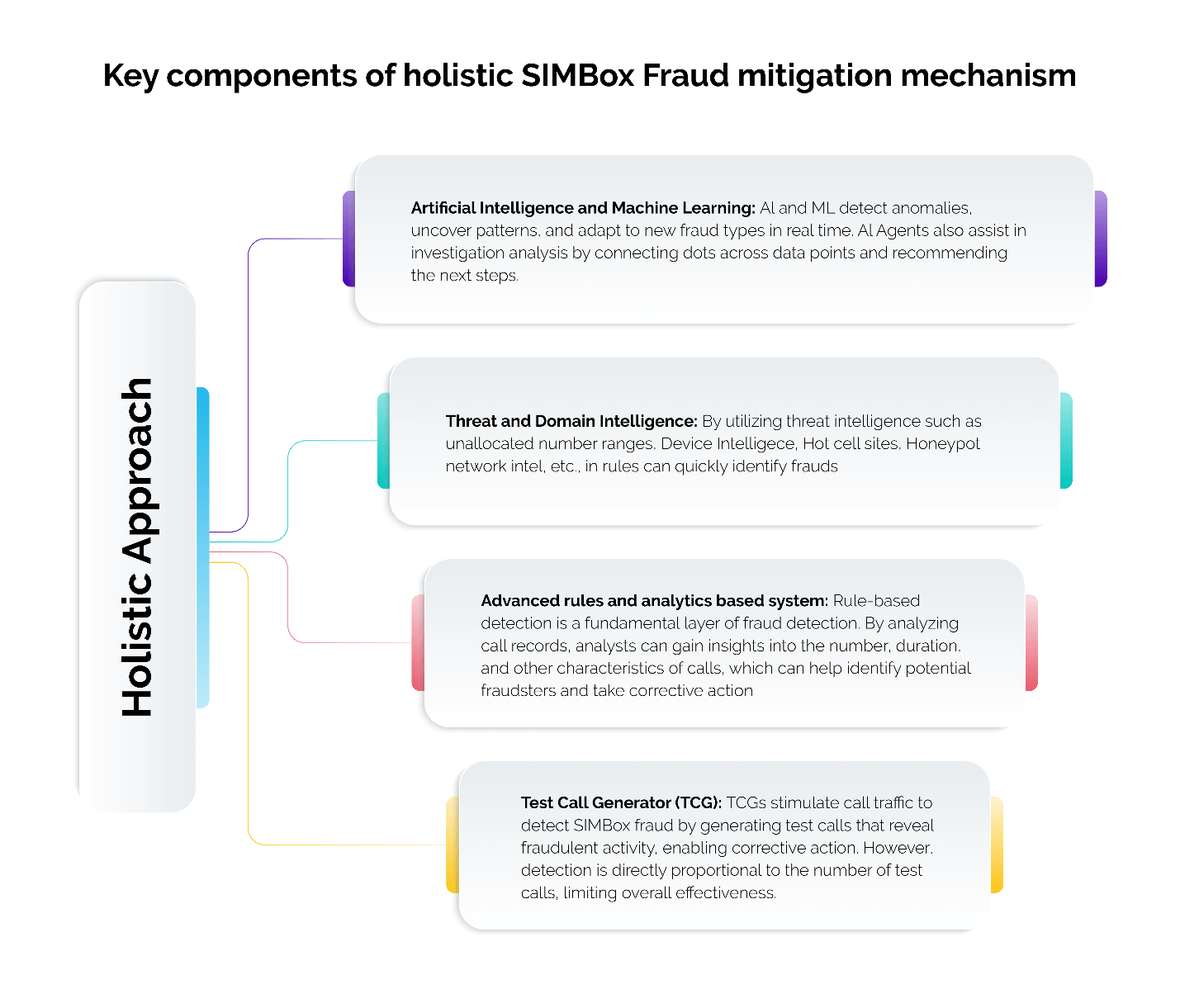
Q6. What are the key components of a holistic SIMBox fraud mitigation system?
Here are the key components of a holistic SIMBox fraud mitigation mechanism:
- Artificial Intelligence and Machine Learning (AI/ML): Detects anomalies, uncovers patterns, adapts to new fraud types in real time, and assists investigations by connecting data points and suggesting next steps.
- Threat and Domain Intelligence: Uses threat intelligence (e.g., unallocated number ranges, device intelligence, hot cell sites and honeypot network) to quickly identify fraud.
- Advanced rules and analytics-based system: Analyzes call records for insights into call volume and patterns.
- Test Call Generator (TCG): Simulates call traffic to identify fraudulent activity.
Want to see how Subex can protect your network from SIMBox fraud?