Combat SIP threats with a Proactive Approach
With the transition from telecom operators to digital service providers, the communication processes and the necessary protocols have changed over the years. The digital information is packetized, wherein the transmission happens over IP packets instead of the earlier circuit-switched transmission. Today, VoIP technology has overshadowed traditional communication technologies, which are comprehensible due to the edge it provides in terms of accessibility, portability, scalability, voice quality, flexibility & lower costs.
While several protocols are used in voice-over-IP (VoIP) communications, Session Initiation Protocol (SIP) has become the most popular. There are various benefits that it brings in for a service provider, which include lower costs, immediate ROI, global potential, mobility & network consolidation.
With the immense benefits that it brings to businesses, there are also certain risks that are associated with it. Security is one such issue that is of paramount importance to the service providers and their customers, as it pertains to direct and indirect attacks by fraudsters and cybercriminals, leading to financial losses and customer churn for the service providers.
Did you know Session Initiation Protocol (SIP) which acts as a signaling protocol for VoIP, is the world’s most hacked protocol?
Let us look at a couple of instances to put this scenario into context.
With Covid-19, SIP has become even more widespread due to the enterprise customers placing more SIP endpoints outside the confines of a logical network. An interesting statistic shows the importance of VoIP security-roughly 46% of illegally made calls across the world involve VoIP technology [1]. As much as 65% of the global DDoS attacks in 2018 were aimed at communication services providers [2].
Also, recently there has been a significant rise in cyber-fraud operations targeting VoIP phone systems worldwide. As per a recent news article, a Gaza-based hacking group was responsible for targeting servers used by more than 1,200 organizations based across over 60 countries, with half of those targets being in the UK. What’s even more worrying is that the hackers worldwide create their own social media groups to share tips and know-how relating to VoIP phone system hacking and organize and coordinate future attacks.
Although most of the telecom networks are still private, but since they also provide SIP trunks as a service to other smaller carriers or enterprises, they end up exposing some part of their network to a public network and thus become vulnerable to attacks. Interconnect using SIP also exposes telecom networks to attacks as the network laid down for immediate partner and telecom may be private and secure, but if the partner’s network is exposed to a public network, it creates a link to telecom’s network to the public network via other carriers. Also, an international call passes through multiple networks before it’s terminated to the destination. All of the carriers may not have the highest level of security. Hence, such calls are vulnerable to eavesdropping and hi-jacking. SIP is intrinsically vulnerable to a range of attacks, and more importantly, the attackers exploit them to instigate direct or indirect losses to service providers. The below diagram depicts the various threats associated with SIP:
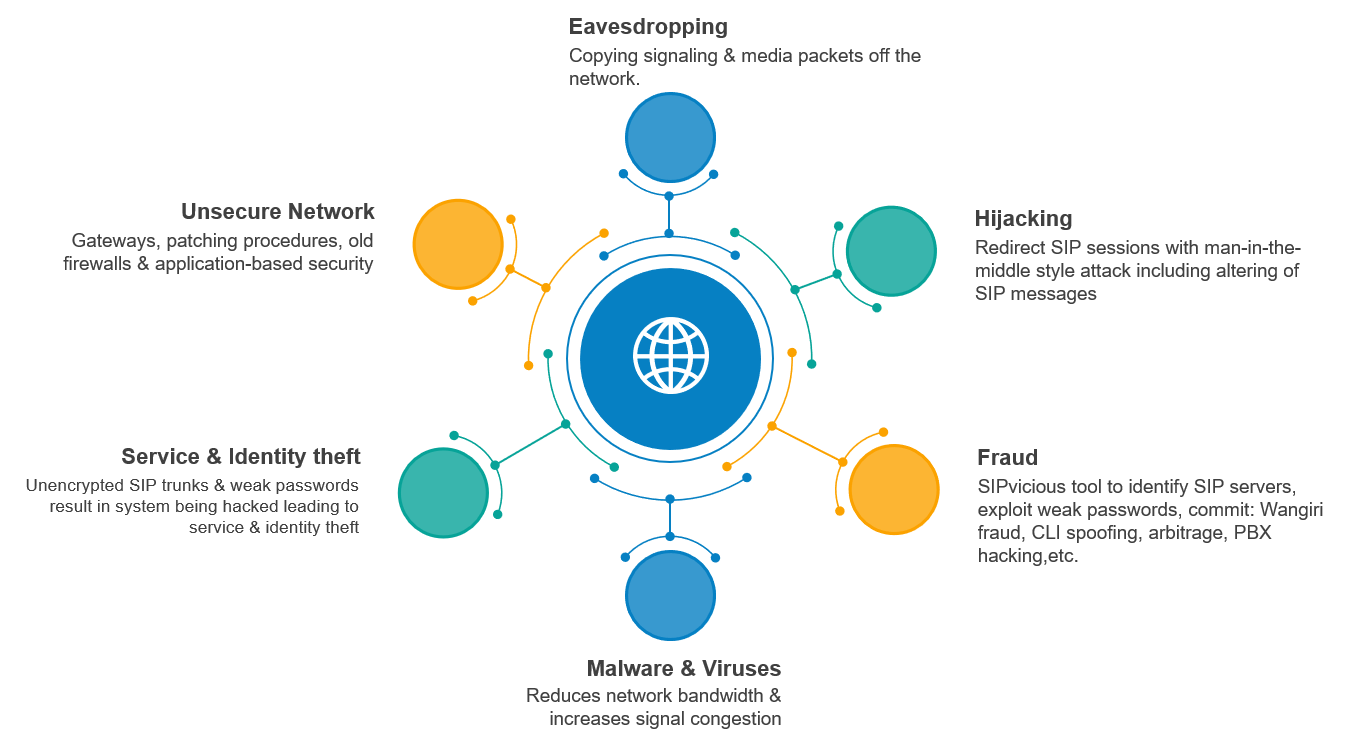
There are several methodologies of preventing SIP vulnerabilities like network firewalls, cybercriminal simulations, software/hardware patches, etc. But the problem with such arrangements is that fraudsters and cyber criminals still find a way to exploit the inherent loopholes of SIP communication.
The need of the hour is a proactive approach to detect and nip the vulnerabilities and risks for a service provider in the bud.
In the traditional approaches, their reactive approach is inadequate and unsatisfactory for the fraud & security strategy of the service providers. This is because of the reliance on xDRs and lack of timely availability of real-time threat intelligence.
However, we believe the way forward is to have a system in place that uses real-time signaling level analysis, complemented with advanced machine learning techniques and real-time threat intelligence, which will provide new opportunities to drive a prevention-based approach and support operators more effectively to address these types of threats.
At Subex, we have over 25 years of experience working with telecom operators to proactively mitigate fraud and security risks. To learn more about our approach, reach out to us, and we will bring our expertise in decoding your troubles.
References:
1. https://startupanz.com/voip-industry-statistics-2020/
Read Our Latest Point of View on SIP Security
Shankha is part of the Pre-sales team. His responsibilities include working closely with sales team and assist in the development of formal sales proposals. He is also involved in qualification of opportunities, building custom demonstrations & solutioning. Shankha graduated from the Gujarat Technological University with degree in Electrical Engineering. He holds an MBA from Symbiosis International, Pune in Digital & Telecom Management.
Request a demo



